hello, can someone help me with it ? sorry for english language, but i can't speak german, but only german people can help me ;(
now i have something like this, when i use
ip route add 165.22.xxx.xxx/32 dev dsl
ip route del default dev dsl
ip route add default dev wg0
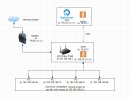
without use ip route i still have provider ip on my fritz, and dont have internet on my pc, only access to lan - 192.168.188.xxx.
i want to get connection like this
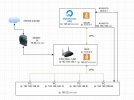
can someone help me with configuration? i want to have vps ip on all my devices in network and acces from vpn to 192.168.188.xxx
ip route without wireguard
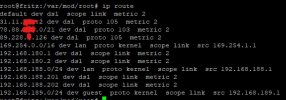
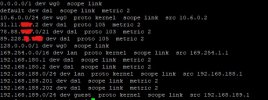
ip route when connected to wireguard server
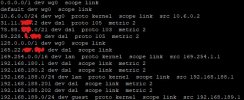
ip route when connected to wireguard server + modified ip routes
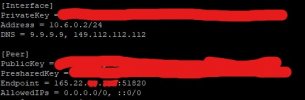
freetz client wireguard
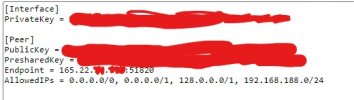
wireguard digitalocean vps server
please help, you can write in german language, i'll translate it
now i have something like this, when i use
ip route add 165.22.xxx.xxx/32 dev dsl
ip route del default dev dsl
ip route add default dev wg0

without use ip route i still have provider ip on my fritz, and dont have internet on my pc, only access to lan - 192.168.188.xxx.
i want to get connection like this

can someone help me with configuration? i want to have vps ip on all my devices in network and acces from vpn to 192.168.188.xxx
ip route without wireguard

ip route when connected to wireguard server

ip route when connected to wireguard server + modified ip routes

freetz client wireguard

wireguard digitalocean vps server

please help, you can write in german language, i'll translate it