Du verwendest einen veralteten Browser. Es ist möglich, dass diese oder andere Websites nicht korrekt angezeigt werden.
Du solltest ein Upgrade durchführen oder ein alternativer Browser verwenden.
Du solltest ein Upgrade durchführen oder ein alternativer Browser verwenden.
zirkon
Aktives Mitglied
- Mitglied seit
- 12 Aug 2008
- Beiträge
- 906
- Punkte für Reaktionen
- 0
- Punkte
- 0
Problem gelöst
Danke für die flotten Antworten.
@olistudent: Static und SSL sind jeweils deaktiviert. Schon klar, dass es keinen Sinn ergibt ohne SSL statisch zu bauen. Habe auch schon make config-clean-deps ausgeführt und das Image neu erstellt. Das Gleiche in Grün. Habe einen Screenshot des Web-Interfaces mal angehängt, wo SSL natürlich nicht mehr zu sehen ist. So bleibt mir nichts anders übrig als die Config selbst zu editieren.

@matze1985: Genau nach dieser Konfigurationsdatei, bzw. dessen Pfad, hatte ich gesucht - danke! Dort ergibt sich dann natürlich ein ganz anderes Bild:
Habe die Einträge nun geändert und die Box neugestartet: Es läuft!
Eigentlich sollte man doch davon ausgehen, dass genau diese Datei beim aktualisieren der Firmware neu erstellt/abgeändert wird - hatte nämlich vorher die SSL-Funktionalität aktiviert, aber eben vor dem "Push" nicht im GUI deaktiviert.
Danke für die flotten Antworten.
@olistudent: Static und SSL sind jeweils deaktiviert. Schon klar, dass es keinen Sinn ergibt ohne SSL statisch zu bauen. Habe auch schon make config-clean-deps ausgeführt und das Image neu erstellt. Das Gleiche in Grün. Habe einen Screenshot des Web-Interfaces mal angehängt, wo SSL natürlich nicht mehr zu sehen ist. So bleibt mir nichts anders übrig als die Config selbst zu editieren.
@matze1985: Genau nach dieser Konfigurationsdatei, bzw. dessen Pfad, hatte ich gesucht - danke! Dort ergibt sich dann natürlich ein ganz anderes Bild:
Code:
export VSFTPD_ALLOW_FTPUSER='no'
export VSFTPD_ANONYMOUS='no'
export VSFTPD_CHROOT='yes'
export VSFTPD_ENABLED='yes'
export VSFTPD_ENABLE_SSL='yes'
export VSFTPD_ENABLE_SSLV2='yes'
export VSFTPD_ENABLE_SSLV3='yes'
export VSFTPD_ENABLE_TLSV1='yes'
export VSFTPD_USERS_ENABLED='yes'Eigentlich sollte man doch davon ausgehen, dass genau diese Datei beim aktualisieren der Firmware neu erstellt/abgeändert wird - hatte nämlich vorher die SSL-Funktionalität aktiviert, aber eben vor dem "Push" nicht im GUI deaktiviert.
- Mitglied seit
- 17 Feb 2007
- Beiträge
- 1,537
- Punkte für Reaktionen
- 0
- Punkte
- 0
diese Einträge werden beim FW-Update nicht angefasst, deswegen sind es ja Konfigurationen.
Die SSL-Einträge bleiben so erhalten und werden entsprechend in die config übernommen, dass sollte natürlich ausgebessert werden, vielleicht schaffe ich es die Tage dass zu machen.
Die SSL-Einträge bleiben so erhalten und werden entsprechend in die config übernommen, dass sollte natürlich ausgebessert werden, vielleicht schaffe ich es die Tage dass zu machen.
C
colonia27
Guest
Hi all, und speziell Darkyputz
die normale vsftpd-Geschicht läuft astrein, nur mit ssl bekomme ich es nicht ans rennen.
Cert+key sind natürlich eingetragen.
Genau wie du Darkyputz wollte ich die Verbindung mit TotalCommander herstellen (gibt einfach kein besseres allround-Tool).
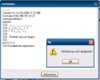
Leider bekomme ich keine Verbindung zustande, siehe bild.
Vllt. kann mir jemand mal screens Freetz-IF des vstfpd schicken damit ich mal die ganzen Häkchen vergleichen kann.
Wird der key bzw. cert auch irgendwo im TC eingestellt? Ich finde da keine Möglichkeit.
guido
die normale vsftpd-Geschicht läuft astrein, nur mit ssl bekomme ich es nicht ans rennen.
Cert+key sind natürlich eingetragen.
Genau wie du Darkyputz wollte ich die Verbindung mit TotalCommander herstellen (gibt einfach kein besseres allround-Tool).
Leider bekomme ich keine Verbindung zustande, siehe bild.
Vllt. kann mir jemand mal screens Freetz-IF des vstfpd schicken damit ich mal die ganzen Häkchen vergleichen kann.
Wird der key bzw. cert auch irgendwo im TC eingestellt? Ich finde da keine Möglichkeit.
guido
Anhänge
sf3978
IPPF-Promi
- Mitglied seit
- 2 Dez 2007
- Beiträge
- 8,014
- Punkte für Reaktionen
- 28
- Punkte
- 48
Wird der key bzw. cert auch irgendwo im TC eingestellt? Ich finde da keine Möglichkeit.
Bei Filezilla ist es so. Ich denke der FTP-Client muss "ssl-fähig" sein.
C
colonia27
Guest
- Mitglied seit
- 17 Feb 2007
- Beiträge
- 1,537
- Punkte für Reaktionen
- 0
- Punkte
- 0
@colonia: beim TC musst du dass nicht angeben er akzeptiert es automatisch, bei mir zu mindest. (Ja ich weiß, ob das richtig ist, ist fraglich)
Poste dochmal deine Config!
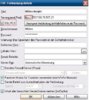
Edit: Deinen Bildern zu folge hast du nicht das richtige SSL-Protokoll erlaubt, hacke mal alle drei an, also SSL2 SSL3 und TSL
Poste dochmal deine Config!
Edit: Deinen Bildern zu folge hast du nicht das richtige SSL-Protokoll erlaubt, hacke mal alle drei an, also SSL2 SSL3 und TSL
C
colonia27
Guest
denke das ist die richtige:
Code:
# cat /var/mod/etc/vsftpd.conf
background=yes
check_shell=no
listen=yes
anonymous_enable=no
local_enable=yes
local_umask=022
chroot_local_user=yes
passwd_chroot_enable=yes
write_enable=yes
banner_file=/etc/motd
nopriv_user=root
secure_chroot_dir=/var/run/vsftpd
listen_port=21
userlist_enable=yes
anon_root=/mod/home/ftp
xferlog_std_format=no
xferlog_enable=yes
vsftpd_log_file=/var/media/ftp/uStor03/FRITZ/logs/vsftpd.log
log_ftp_protocol=no
syslog_enable=no
max_clients=25
max_per_ip=5
pasv_min_port=21212
pasv_max_port=21262
pasv_promiscuous=yes
delay_failed_login=15
chroot_list_enable=yes
ssl_enable=yes
ssl_sslv2=yes
ssl_sslv3=yes
ssl_tlsv1=yes
force_local_data_ssl=yes
force_local_logins_ssl=yes
pasv_address=xx.xx.xx.xxsf3978
IPPF-Promi
- Mitglied seit
- 2 Dez 2007
- Beiträge
- 8,014
- Punkte für Reaktionen
- 28
- Punkte
- 48
Hier meine conf:
[Edit frank_m24: Bitte benutzt CODE Tags für solche Ausgaben.]
[Edit frank_m24: Bitte benutzt CODE Tags für solche Ausgaben.]
Code:
# cat /var/mod/etc/vsftpd.conf
background=yes
check_shell=no
listen=no
anonymous_enable=no
local_enable=yes
local_umask=022
chroot_local_user=no
passwd_chroot_enable=no
write_enable=yes
banner_file=/etc/motd
nopriv_user=root
secure_chroot_dir=/var/run/vsftpd
listen_port=xxxx
userlist_enable=yes
anon_root=/mod/home/ftp
xferlog_std_format=no
xferlog_enable=yes
vsftpd_log_file=/var/media/ftp/uStor01/vsftpd.log
log_ftp_protocol=yes
syslog_enable=no
max_clients=25
max_per_ip=5
pasv_min_port=0
pasv_max_port=0
pasv_promiscuous=no
delay_failed_login=15
chroot_list_enable=yes
ssl_enable=yes
ssl_sslv2=yes
ssl_sslv3=yes
ssl_tlsv1=yes
force_local_data_ssl=yes
force_local_logins_ssl=yes
hide_file={*.cfg,*.conf,passwd,group,vsftpd.user_list,etc,usr,ftpuser,ftpuser1,vsftpd_user_conf,hosts.allow,hosts.deny}
userlist_deny=no
userlist_file=/var/mod/etc/vsftpd.chroot_list
user_config_dir=/var/media/ftp/uStor01/vsftpd_user_conf
cmds_allowed=PASV
log_ftp_protocol=yes
tcp_wrappers=yes
C
colonia27
Guest
hier mal ein Teil (und wahrscheinlich der relevante) deiner Config
was sagen mir die roten Abschnitte?
und diesen Teil hatte ich eben wohl bei mir abgeschnitten
Code:
ssl_enable=yes
ssl_sslv2=yes
ssl_sslv3=yes
ssl_tlsv1=yes
force_local_data_ssl=yes
force_local_logins_ssl=yes
[COLOR=Red]hide_file={*.cfg,*.conf,passwd,group,vsftpd.user_list,etc,usr,ftpuser,ftpuser1,vsftpd_user_conf,hosts.allow,hosts.deny}[/COLOR]
userlist_deny=no
userlist_file=/var/mod/etc/vsftpd.chroot_list
user_config_dir=/var/media/ftp/uStor01/vsftpd_user_conf
cmds_allowed=PASV
log_ftp_protocol=yes
[COLOR=Red]tcp_wrappers=yes[/COLOR]und diesen Teil hatte ich eben wohl bei mir abgeschnitten
Code:
userlist_file=/var/media/ftp/uStor01/configs/vsftpd.user_list
userlist_deny=no
userlist_enable=yes- Mitglied seit
- 17 Feb 2007
- Beiträge
- 1,537
- Punkte für Reaktionen
- 0
- Punkte
- 0
Hmm, gleiche Konfig wie bei mir.
Hast du ein Zertifikat im Webif eingetragen?
Das sollte als nächstes kommen.
edit: das ist denke ich nicht der unterschied, er läst es über tcpwrapper laufen um die hosts einzuschränken, dass brauchst du nicht.
Hast du ein Zertifikat im Webif eingetragen?
Das sollte als nächstes kommen.
edit: das ist denke ich nicht der unterschied, er läst es über tcpwrapper laufen um die hosts einzuschränken, dass brauchst du nicht.
sf3978
IPPF-Promi
- Mitglied seit
- 2 Dez 2007
- Beiträge
- 8,014
- Punkte für Reaktionen
- 28
- Punkte
- 48
Die roten Abschnitte:
Aus man vsftpd.conf
Aus man vsftpd.conf
hide_file
This option can be used to set a pattern for filenames (and directory names etc.) which should be hidden from directory listings. Despite being hidden, the files / directories etc. are fully accessible to clients who know what names to actually use. Items will be hidden if their names contain the string given by hide_file, or if they match the regular expression specified by hide_file. Note that vsftpd's regular expression matching code is a simple implementation which is a subset of full regular expression functionality. Example: hide_file={*.mp3,.hidden,hide*,h?}
Default: (none)
tcp_wrappers
If enabled, and vsftpd was compiled with tcp_wrappers support, incoming connections will be fed through tcp_wrappers access control. Furthermore, there is a mechanism for per-IP based configuration. If tcp_wrappers sets the VSFTPD_LOAD_CONF environment variable, then the vsftpd session will try and load the vsftpd configuration file specified in this variable.
Default: NO
C
colonia27
Guest
da ich wusste das diese Frage kommt, hatte ich das gleich in meinem ersten post erwähnt ;-)
Wie bekomme ich denn dieses key+cert in Filezilla eingebunden?
[EDIT] also sind hide_files und tcp_wrappers nicht für ssl relevant !?! So versteh ich das zumindest
Wie bekomme ich denn dieses key+cert in Filezilla eingebunden?
[EDIT] also sind hide_files und tcp_wrappers nicht für ssl relevant !?! So versteh ich das zumindest
sf3978
IPPF-Promi
- Mitglied seit
- 2 Dez 2007
- Beiträge
- 8,014
- Punkte für Reaktionen
- 28
- Punkte
- 48
Wie bekomme ich denn dieses key+cert in Filezilla eingebunden?
[EDIT] also sind hide_files und tcp_wrappers nicht für ssl relevant !?! So versteh ich das zumindest
Welchen Servertyp hast Du in Filezilla gewählt? Du bekommst eine Anfrage von Filezilla betr. Zertifikat, das Du akzeptieren oder ablehnen kannst.
Ja, hide_files und tcp_wrappers sind für ssl nicht relevant.
C
colonia27
Guest
Servertyp: SFTP - SSH......
Code:
Status: Connecting to 192.168.78.101...
Antwort: fzSftp started
Befehl: open "[email protected]" 22
Spur: Looking up host "192.168.78.101"
Spur: Connecting to 192.168.78.101 port 22
Spur: Server version: SSH-2.0-dropbear_0.52
Spur: Using SSH protocol version 2
Spur: We claim version: SSH-2.0-PuTTY_Local:_Sep_15_2008_15:22:02
Spur: Using Diffie-Hellman with standard group "group1"
Spur: Doing Diffie-Hellman key exchange with hash SHA-1
Spur: Host key fingerprint is:
Spur: ssh-rsa 1039 xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx
Spur: Initialised AES-256 SDCTR client->server encryption
Spur: Initialised HMAC-SHA1 client->server MAC algorithm
Spur: Initialised AES-256 SDCTR server->client encryption
Spur: Initialised HMAC-SHA1 server->client MAC algorithm
Befehl: Pass: *************
Spur: Sent password
Spur: Access granted
Spur: Opened channel for session
Spur: Primary command failed; attempting fallback
Spur: Started a shell/command
Status: Connected to 192.168.78.101
Spur: Server sent command exit status 2
Spur: Disconnected: All channels closed
Fehler: Fatal: unable to initialise SFTP on server: could not connect
Fehler: Verbindung mit Server fehlgeschlagensf3978
IPPF-Promi
- Mitglied seit
- 2 Dez 2007
- Beiträge
- 8,014
- Punkte für Reaktionen
- 28
- Punkte
- 48
Servertyp: SFTP - SSH......
Versuch mal im Filezilla mit Servertyp: FTPES
EDIT: Hast Du auch dropbear mit SFTP (statisch) auf der Box?
C
colonia27
Guest
Hatte ich auch schon versucht, sieht dann so aus:
Die Anzeige des FREETZ stimmt mich zuversichtlich, aber ganz hauts noch nicht hin
Code:
Status: Connecting to 192.168.78.101:21...
Status: Verbindung hergestellt, warte auf Willkommensnachricht...
Antwort: 220- __ _ __ __ ___ __
Antwort: 220- |__ |_) |__ |__ | /
Antwort: 220- | |\ |__ |__ | /_
Antwort: 220-
Antwort: 220- The fun has just begun...
Antwort: 220
Befehl: AUTH TLS
Antwort: 234 Proceed with negotiation.
Status: Starte TLS...
Spur: GnuTLS error -9: A TLS packet with unexpected length was received.
Fehler: Verbindung mit Server fehlgeschlagensf3978
IPPF-Promi
- Mitglied seit
- 2 Dez 2007
- Beiträge
- 8,014
- Punkte für Reaktionen
- 28
- Punkte
- 48
Bei mir sieht das so aus:
EDIT: Wie hast Du das Zertifikat und den Schlüssel für vsftpd erstellt?
Code:
Status: Verbinde mit 192.168.xxx.xxx:yyy...
Status: Verbindung hergestellt, warte auf Willkommensnachricht...
Antwort: 220- __ _ __ __ ___ __
Antwort: 220- |__ |_) |__ |__ | /
Antwort: 220- | |\ |__ |__ | /_
Antwort: 220-
Antwort: 220- The fun has just begun...
Antwort: 220
[B]Befehl: AUTH TLS
Antwort: 234 Proceed with negotiation.
Status: Initialisiere TLS...
Status: Überprüfe Zertifikat...[/B]
Befehl: USER ###########
[B]Status: TLS/SSL-Verbindung hergestellt.[/B]
Antwort: 331 Please specify the password.
Befehl: PASS ********
Antwort: 230 Login successful.
Befehl: SYST
Antwort: 215 UNIX Type: L8
Befehl: FEAT
Antwort: 211-Features:
Antwort: AUTH SSL
Antwort: AUTH TLS
Antwort: EPRT
Antwort: EPSV
Antwort: MDTM
Antwort: PASV
Antwort: PBSZ
Antwort: PROT
Antwort: REST STREAM
Antwort: SIZE
Antwort: TVFS
Antwort: UTF8
Antwort: 211 EndEDIT: Wie hast Du das Zertifikat und den Schlüssel für vsftpd erstellt?
C
colonia27
Guest
OT: Wir sind gerade in unserer post-Anzahl synchron 
Zumindest wenn du auch OT antwortest.
Denke ich werd mich morgen mit meinem Problem weiter beschäftigen.
Sooo steinig kann der Weg nicht mehr sein, wo ich schon das Freetz-Banner sehe ;-)
Also, vielen Dank erstmal für deine Hilfe. Cu
Guido
[EDIT] so wies im IF angegeben ist:
und dann das ganze Ding mit C&P eingefügt.
Zumindest wenn du auch OT antwortest.
Denke ich werd mich morgen mit meinem Problem weiter beschäftigen.
Sooo steinig kann der Weg nicht mehr sein, wo ich schon das Freetz-Banner sehe ;-)
Also, vielen Dank erstmal für deine Hilfe. Cu
Guido
[EDIT] so wies im IF angegeben ist:
Code:
openssl req -new -x509 -nodes -out vsftpd.pem -keyout vsftpd.pemNeueste Beiträge
-
Minitelefonanlage
- Letzte: Eklypter
-
HIRE A HACKER TO HACK AND SPY ON PHONE; CYBERPUNK PROGRAMMERS
- Letzte: jenniferjemma029
-
-
[Sammlung] Aktuelle Konditionen für DSL-Vertragsverlängerung
- Letzte: FrancisFree
-
[Frage] Rufumleitung über Fritzbox kostenlos?
- Letzte: totalverrückteruser
-
Forum extrem langsam seit 29.01.12
- Letzte: Novize